|
||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Rutgers:
Spring 2005
Rutgers School of Law - Newark Fall 2005 Semester Internet Law Seminar Course Outline and Schedule
August 25 I Introduction to the Internet and Internet Law.
1."Why Should the Internet Be Any Different" Pace Law Review (Fall 1998) Please note this and other articles which were written by Jonathan Bick may be found on BickLaw.com at http://www.bicklaw.com/Publications/index.html.
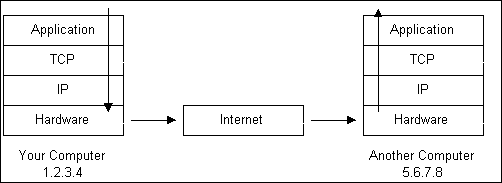
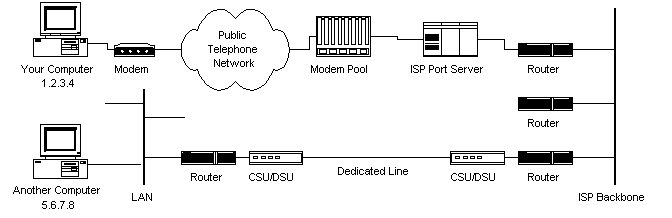
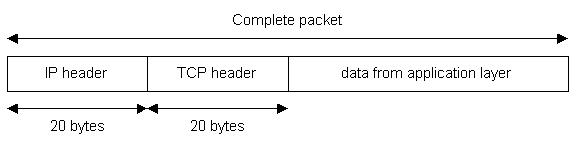
2. Let’s Get Technical (Course Materials 1)
3. Current Internet Laws -- see http://uscode.house.gov (Course Materials 2) 4. Pending Internet Law Snap Shot -- see http://thomas.loc.gov/ (Course Materials 3) Review Text Topics … Chapters 1 - 10 Please note that the numbers which follow refer to chapters in 101 Things You Need To Know About Internet Law by Jonathan Bick (Random House 2000)
1. A parent is almost never liable for a child's bad acts on the Internet
2. To make Internet contracts enforceable, simply have proof of written signed terms
3. To avoid out-of-state liability when using web ads, avoid out-of-state contacts
4. Web site advertisement publishers are almost never liable for customers' advertisements
5. What can legally be done if a person impersonates another on the Internet
6. Buying and selling medicine on the Internet is legal
7. Spamming is generally not illegal, but one California court ruled spam e-mail to be illegal trespass
8. Sweepstakes and other Internet games of chance are legal
9. An Internet site's activities can result in an out-of-state suit....
10. Internet credit card transactions will be afforded the same standard of protection as all other credit card transactions
Start research logs and outlines
September 1 II Elements of electronic commerce
1. Is your Client a Spammer? New Jersey Law Journal October 18, 2004 http://www.bicklaw.com/Publications/client_a_spammer.htm
2.Franchise Law Applies to Internet New Jersey Law Journal September 20, 2004 http://www.bicklaw.com/Publications/Franchise_Law.htm
3. Legality of Internet Wine Sales in Flux New Jersey Law Journal July 19, 2004 http://www.bicklaw.com/Publications/Legality_internet_sales.htm
4.Granholm v. Heald, 125 S. Ct. 1885 (U.S., 2005) -- State laws allowed in-state wineries to make direct sales to customers. They force out-of-state wineries to make sales only through wholesalers and retailers at greater expense. The wineries contended that the regulatory schemes discriminated against interstate commerce. States argued that the schemes were necessary to prevent underage persons from purchasing wine and to promote the collection of taxes. The Court held that the state laws discriminated against interstate commerce. It also found that the discrimination was not authorized by U.S. Const. amend XXI, § 2.
5. e-Credit Card Contract The Internet Newsletter November 2001 volume 6, Number 8 American Lawyer Media http://www.bicklaw.com/Publications/e-credit.htm
6. Purchase of Medications Online is Lawful New Jersey Law Journal April 9, 2004 http://www.bicklaw.com/Publications/medications_purchase_online.htm
7. E-Commerce Insurance New Jersey Law Journal August 19, 2002 http://www.bicklaw.com/Publications/e-commerce_insurance.htm
8. E-Outsourcing New Jersey Law Journal October 29, 2001 http://www.bicklaw.com/Publications/e-outsourcing.htm
9. Funding e-Firms The Daily Deal October 23, 2001 Tuesday http://www.bicklaw.com/Publications/funding%20e-firms.htm
Review Text Topics … Chapters 11 – 20
11. Trademark names and e-linking are subject to legal scrutiny
12. Internet banking is legal
13. Unencrypted Internet communication is not usually protected by attorney-client privilege
14. Internet business methods can be patented
15. License don't sell-Internet domain names
16. Internet privacy rights are scarce
17. E-commerce data collection is subject to legal limitations
18. The Constitution limits a court's ability to make an Internet site owner subject to an out-of-state suit
19. Internet repossessions are legal
20. Internet service providers (ISPs) are protected from legal liability for certain actions of their clients
Hand in copy of research log review (optional) September 8 III Electronic commerce
1. AMERICANS WITH DISABILITIES ACT AND THE INTERNET Copyright (c) 2000 Albany Law Journal of Science & Albany Law Journal of Science & Technology 2000 10 Alb. L.J. Sci. & Tech. 205 http://www.bicklaw.com/Publications/ADA.htm
2. "Due Diligence for 'Dot-Com' Deals", Due Diligence New York Law Journal, May 18, 1999 http://www.bicklaw.com/Publications/Due_diligence.htm.
3."Coping With COPPA New Jersey Law Journal December 29, 2003 http://www.bicklaw.com/Publications/Coping_with_COPPA.htm.
4. How e-Commerce Laws Can Increase the Digital Divide NATOA Journal of Municipal Telecommunication Policy December 2000. http://www.bicklaw.com/Publications/Digital_divide.htm
5.e-Dissemination The Internet Newsletter October 2001 volume 6, Number 7 American Lawyer Media -- Securities Law Avoiding the Violations Risked by Companies That Use the Web to Disseminate Information http://www.bicklaw.com/Publications/e-dissemination.htm
6. Funding e-Firms The Daily Deal October 23, 2001 Copyright 2001 The Deal L.L.C. http://www.bicklaw.com/Publications/funding%20e-firms.htm
7. Unauthorized Practice of Law Comm. v. Parsons Tech., Inc.Civil Action No. 3:97-CV-2859-H UNITED STATES DISTRICT COURT FOR THE NORTHERN DISTRICT OF TEXAS, DALLAS DIVISION 1999 U.S. Dist. LEXIS 813 -- Defendant offered a computer software program that included legal forms along with instructions. Plaintiffs, the unauthorized practice of law committee, brought suit alleging that the selling of defendant's program violated Texas' unauthorized practice of law statute. The court granted plaintiffs' motion. The court found that the program violated the unauthorized practice of law statute because the preparation of legal instruments of all kinds involves the practice of law.
Vacated by, Remanded by: Unauthorized Practice of Law Comm. v. Parsons Tech., Inc., 179 F.3d 956, 1999 U.S. App. LEXIS 14234 (5th Cir. Tex. 1999) -- Plaintiff moved to enjoin defendant corporation from selling and distributing software programs entitled "Quicken Family Lawyer." The district court granted the motion. The court vacated the injunction and judgment. The state legislature, subsequent to the filing of defendant's appeal, had enacted an amendment to Tex. Govt. Code Ann. § 81.101 (1998). The amendment, H.R. 1507, 76th Leg., Reg. Sess. (Tex. 1999), stated that the practice of law did not include the sale or distribution of computer software if the products stated clearly and conspicuously that the products were not a substitute for the advice of an attorney.
8.“Internet Merchant Service Agreements” September 2001 E-Commerce Supplement American Law Media http://www.bicklaw.com/Publications/Merchant_Service_Agreements.htm
Review Text Topics … Chapters 21 – 30
21. Protect domain names by securing trademark rights first
22. An Internet service agreement has some standard elements. .
23. Legal notices that are properly placed on a web site will minimize or eliminate legal liability
24. Changes in trademark laws have resulted in changes in domain name dispute outcomes
25. Internet telemedicine patients have fewer rights than traditional patients
26. Applying suitability legal concept to e-stock brokers
27. Current laws do not fully protect the privacy of information in the possession of an Internet service provider
28. Workplace privacy is nearly nonexistent
29. The Internet may soon be deemed a public accommodation for the visually impaired
30. Personal jurisdiction are in flux with respect to the Internet
Hand in copy of the guided research paper outline for review September 15 IV Electronic contracts
1, Viable E-signature Options The Copyright & New Media Law Newsletter July 2004 http://www.bicklaw.com/Publications/Viable_e-signature.htm
2.UCC section 2B (November 1,1997 Draft) … first page included … see www.law.uh.edu/ucc2b/110197/full.html
3. La Mar Hosiery Mills v. Credit & Commodity Corp.,28 Misc. 2d. 765; 216 N.Y.S. 2d 186) - guarantee in the form of a telegram satisfies State of Frauds' writing and signature requirements
4.People v.Hagan, 556 N.E.2d 1224, (Ill. App. 1990) - comparing fax and telegram technology
5. Brian Jackson v. Encyclopaedia Britannica Education Corp. 1996 U.S. Dist. LEXIS 571 (1-22-1996) - application of writing and signature requirements
6. People v. Avila, 770 P.2d 1330 (Col. App 1988) - court holds that data stored on a computer disk satisfies "written instrument" requirement of forgery statute
7. ProCD, Inc. v. Matthew Zeidenberg and Silken Mountain Web Services, 86 F.3d 1447 (7th Cir. 1996) point and click agreements
8.Compuserve v. Patterson, 89 F.3d 1257 (6th Cir. 1996) - point and click contract terms
9. Cal. Gov. Code Section 16.5 (1995) - digital signatures are ok when specifically authorized
Review Text Topics … Chapters 31 – 40
31. The Internet can provide legal notice
32. Consider European comparative advertising legal limitations when preparing Internet advertisements
33. Commercial Internet web site content is protected by the First Amendment
34. Internet auctions result in legal contracts
35. Internet transactions can result in "choice-of-law" difficulties.
36. U.S. legal limitations apply to international Internet services
37. International law limits use of Internet digital signatures
38. State laws limit physicians' use of the Internet
39. European Internet signature legal limitations differ among countries
40. International laws extend Internet service providers' content liability
Outlines returned with comments (not graded ) September 22 V Miscellaneous e-topics
1. Internet Charity Registration Requirements New Jersey Law Journal May 9, 2005 http://www.bicklaw.com/InternetCharityRules.htm
2. Inheriting Deceased's E-mail New Jersey Law Journal March 7, 2005 http://www.bicklaw.com/Publications/InheritingDeceasedsE-mail.htm
3. Matrimonial Lawyers Have a New Tool New Jersey Law Journal January 3, 2005 http://www.bicklaw.com/Publications/e-MatrimonialLaw.htm
4. RIAA Suits The Internet Newsletter September 26, 2003 http://www.bicklaw.com/Publications/RIAA_Suits.htm
5. The Recording Industry Association of America Sues Its Members' Customers New Jersey Law Journal November 3, 2003 http://www.bicklaw.com/Publications/E-download_suits.htm
6. Top HR E-Laws New Jersey Law Journal June 9, 2003 http://www.bicklaw.com/Publications/Top_HR_e-laws.htm
7. Internet Coming into Play - Internet and Real Estate New York Law Journal, August 14, 2000
Review Text Topics … Chapters 41 – 50
41. Most proposed Internet legislation is not likely to be implemented
42. Digital certificates do not usually provide significant legal rights
43. Internet loans are lawful
44. Internet insurance addresses new risk
45. Internet wagering is generally illegal
46. Some Internet content is legally free to use
47. Internet nondisclosure agreements have unique features
48. Internet investment advisers require special legal precautions
49. Taxation of European e-commerce differs among countries
50. Using Internet materials may increase legal risk
Hand in list of target publications September 29 VI Intellectual property protection
1. METRO-GOLDWYN-MAYER STUDIOS INC., ET AL., PETITIONERS v. GROKSTER, LTD., ET AL. SUPREME COURT OF THE UNITED STATES 125 S. Ct. 2764; 162 L. Ed. 2d 781; June 27, 2005
Users employed their free software primarily to download copyrighted files. Software distributors contended that they could not be liable for the users' infringements since the software was capable of substantial non-infringing uses. The U.S. Supreme Court found distributors liable for contributory infringement, regardless of the software's lawful uses, based on evidence that the software was distributed with object of promoting infringement.
2. Trademark Law Shapes Internet Pop-up Ads New Jersey Law Journal June 13, 2005 http://www.bicklaw.com/PopUpandTM.htm
3. Exploration of Trademarks on the Internet New Jersey Law Journal December 8, 2003 http://www.bicklaw.com/Publications/Exploration_trademarks_over_internet.htm
4. Copyrighting e-Content New Jersey Law Journal July 22, 2002 http://www.bicklaw.com/Publications/Copyrighting_e-content.htm
5. Beethoven.Com LLC., et al., Petitioners v. Librarian of Congress, Respondent, American Federation of Television and Radio Artists, et al., Intervenors 394 F.3d 939
Copyright owners challenged Librarian of Congress right to set copyright license rates for web-casters based on Copyright Arbitration Royalty Panel (CARP). Prior to CARP petitioner negotiated agreements, which were submitted to the CARP as evidence of market valuation. The CARP rejected most of the rates in agreements. The court held that the non-participant owners lacked standing to challenge the Librarian's order because they were not parties to the CARP proceedings. The court found it proper to vacate the determination of the effective date for the payment of royalty rates. The court upheld the Librarian's order because the Librarian offered a facially plausible explanation for the determination based on the record.
6. “A Terse Guide to the e-Application of the Digital Millennium Copyright Act” Rutgers Computer and Technology Law Journal, June 2001, 27 Rutgers Computer & Tech. L.J. ___; http://www.bicklaw.com/Publications/DMCA_Guide.htm
7. e-Publications New Jersey Law Journal, November 20, 2000 http://www.bicklaw.com/Publications/e-Pubications.htm
8. Spammers Should Know Their Source New Jersey Law Journal April 11, 2005 http://www.bicklaw.com/SpamTargetSource.htm
9. Protecting Internet Communications New Jersey Law Journal January 17, 2005 http://www.bicklaw.com/Publications/ProtectingInternetCommunications.htm
Submit guided research paper draft ( mandatory … graded )
Review Text Topics … Chapters 51 – 60
51. E-business is particularly susceptible to nine legal perils
52. International program license agreements are important for e-commerce outside of the U.S
53. The responsibility for content control by Internet service providers varies in Europe
54. Some countries legally protect personal data stored on the Internet
55. Worldwide Internet e-data legal protection varies
56. Internet signatures can be legally acceptable
57. Internet patents are subject to legal testing
58. Internet proxies are lawful
59. Internet intellectual property transfers must apply state law ...
60. Internet message encryption laws diverge October 6 VII The tax man cometh to cyberspace
1. Implementing e-Commerce Tax Policy, Harvard Journal of Law and Technology Volume 13, Number 3 Summer 2000 13 Harv. J. Law & Tec. ___. Spring 2000. http://www.bicklaw.com/Publications/e-commerce_tax_policy.htm
2. "Internet Access Service Not Subject to Sales Tax", NYLJ, June 19, 1997 page 5 (Course Materials 4)
3. Licensing Domain Name New York Law Journal, August 24, 1999 http://www.bicklaw.com/Publications/License_domain_Name.htm
4. Internet Tax Freedom Act. Act Oct. 21, 1998, P.L. 105-277, Div C, Title XI, 112 Stat. 2681-719; Nov. 28, 2001, P.L. 107-75, § 2, 115 Stat. 703; Dec. 3, 2004, P.L. 108-435, §§ 2-6A, 118 Stat. 2615 (effective 11/1/2003, as provided by § 8 of such Act) (Course Materials 5)
Review Text Topics … Chapters 61 – 70
61. Internet chemical purchases are subject to recipients' jurisdictional rules
62. International e-privacy laws are primarily voluntary
63. International e-copyright laws are in flux
64. Clicking "I agree" has different meanings around the world ...
65. Global e-buyers beware
66. International e-broadcasting legal rules are country specific..
67. Special legal liability is associated with e-promotions
68. Typical domain name cease-and-desist letter and an appropriate reply
69. Reply to domain name cease-and-desist letter
70. FCC has begun to regulate the Internet
Feedback given on guided research paper draft (mandatory)
October 13 VIII Online crime
1.“Avoiding e-Security Violations” NJLJ July 2, 2001 http://www.bicklaw.com/Publications/e-securities.htm
2. A Hole in the CAN-SPAM Act New Jersey Law Journal May 10, 2004 http://www.bicklaw.com/Publications/hole_in_CAN-SPAM.htm
3. Circumventing the CAN-SPAM Act New Jersey Law Journal March 5, 2004 http://www.bicklaw.com/Publications/Circumventing_CAM-SPAM-Act.htm
4. e-Respondeat Superior New Jersey Law Journal August 26, 2002 http://www.bicklaw.com/Publications/e-respondeat_superior.htm
5. People v. Avila, 770 P.2d 1330 (Col. App 1988) - court holds that data stored on a computer disk satisfies "written instrument" requirement of forgery statute
6. TITLE 18. CRIMES AND CRIMINAL PROCEDURE PART I. CRIMES CHAPTER 47. FRAUD AND FALSE STATEMENTS (Course Materials 6)
Review Text Topics … Chapters 71 – 80
71. Selling wine via the Internet is lawful
72. E-commerce infrastructure builder contracts require special elements
73. Forty-three state laws recognize digital signatures
74. The Federal Trade Commission has begun to regulate the Internet
75. The Internet is a litigation tool
76. The Internet is an evidentiary source
77. Internet legal evidence results in new legal difficulties
78. Promotion agency agreements for Internet services are advisable
79. e-mail is legally discoverable
80. Internet crimes and violations are emerging
Schedule feedback meetings October 20 IX Internet speech
1. Reno v. ACLU, 521 U.S. 844 (U.S., 1997) The Supreme Court has rejected attempts to extend the broadcast regime to the Internet.
2. American Libraries Ass'n v. Pataki, 969 F. Supp. 160 (S.D.N.Y. June 20, 1997).
Plaintiffs filed an action challenging N.Y. Penal Law § 235.21(3), which was an attempt to keep people from transmitting material harmful to minors via the Internet. The basis of seeking relief was that the Act burdened free speech contrary to U.S. Const. amend. I and also burdened interstate commerce in violation of the Commerce Clause.
3. Political Spam New Jersey Law Journal February 7, 2005 http://www.bicklaw.com/Publications/PoliticalSpam.htm
4. In Dow Jones & Co. v. Gutnick, Australia High Court [2002] H.C.A. 56 The Australian High Court held that Australian courts have jurisdiction over a claim of defamation based on material that was placed on the Internet outside of Australian borders. http://www.securitymanagement.com/library/Dow_Gutnick0403.pdf#search='Dow%20Jones%20&%20Co.%20v.%20Gutnick' (last visited 8/1/05)
5. E-Broadcast New Jersey Law Journal July 22, 2003 http://www.bicklaw.com/Publications/e-broadcast.htm
Review Text Topics … Chapters 81 – 90
81. Reducing e-law risks is possible
82. Dot.com liability insurance contracts address legal risk
83. Copying, printing, and redistributing e-data are generally lawful
84. How can I protect my name on the Internet? Register it with many variations
85. Additional legal activity may be required to protect certain e-names
86. What can be done if someone links to a web site without permission?
87. Using the Internet to find Internet law is easy but may be inaccurate
88. Legally assigning Internet content usually requires a customized contract
89. Internet hijacking is unlawful without consent
90. Unauthorized framing is usually unlawful
October 27 X Cyber-torts
1. Cubby, Inc. v. Compuserve, Inc., 776 F. Supp. 135 (S.D.N.Y. 1991)
The court though a defamation and not a copyright action, addressed the issue of what knowledge should be attributed to an online service provider with respect to the allegedly defamatory comments posted on the Internet and made available through CompuServe
A database operator brought an action against another database owner for libel, business disparagement, and unfair competition arising from carrying in its database a publication containing allegedly defamatory statements about plaintiffs.
2. Client Internet Services Expose Firms to New Liability New Jersey Law Journal September 20, 2004 http://www.bicklaw.com/Publications/Client_internet_to_Liability.htm
3.e-TrespassNew York Law Journal, August 21, 2000 http://www.bicklaw.com/Publications/e-trespass.htm
4. eBay, Inc. v. Bidder's Edge, Inc., 100 F. Supp. 2d 1058 (N.D. Cal. 2000).
An internet-based trading site, brought suit against an internet-based aggregation site, seeking to prevent use of an automated querying program. Nine causes of action: trespass, false advertising, federal and state trademark dilution, computer fraud and abuse, unfair competition, misappropriation, interference with prospective economic advantage and unjust enrichment.
5. Pop-up Advertisement Litigation Strategies New Jersey Law Journal July 19, 2004 http://www.bicklaw.com/Publications/Pop-op.htm
6. Spam Class Actions New Jersey Law Journal May 5, 2003 http://www.bicklaw.com/Publications/spam_class_action.htm
7. Stop Bad e-Publicity New Jersey Law Journal January 28, 2002 http://www.bicklaw.com/Publications/Stop_Bad_e-publicity.htm
Review Text Topics … Chapters 91 –100
91. Image (IMG) links normally increase legal liability
92. Offering securities through the Internet has legal limitations
93. E-notices help protect copyrights
94. Internet publicity releases help to limit legal liability
95. E-content writer's contract may be a work-for-hire agreement
96. Internet employment services agreements usually protects one party
97. Securities brokers' obligations apply to clients' Internet trading
98. Web Trust seal providers are liable to the public
99. Obscenity and indecency e-content regulation on the Internet is in flux
100. Some public access to the Internet is legally limited
November 3 XI Electronic mail and data privacy
1.United State Privacy Act U.S.C. 5 USCS § 552a (2005) (Course Material 7)
The Privacy Act prohibits nonconsensual disclosure of personal information, but is subject to numerous exemptions. One of these, the routine use exemption, permits nonconsensual disclosure of personal information where the purpose for collection is compatible with its use by the federal agency.
2. The Electronic Communications Privacy Act (CPA) 18 U.S.C. Section 2703 (Course Material 8)
With respect to stored e-mail, see 18 U.S.C. 2703(a), (b) (2000) (authorizing, under the Electronic Communications Privacy Act (ECPA), subpoenas for e-mail that has been sitting on a server for longer than 180 days without being opened and for e-mail that the recipient has accessed and stored on an outside server for any length of time). If the information is stored with a service not available to the general public (e.g., one run by an employer), then the government may obtain the stored information (content or identifying) simply upon a request. See 2703(a)(1)-(3). With respect to Internet Service Provider logs (authorizing access to these records if the government alleges that the records are "relevant and material to an ongoing criminal investigation").
3. McVeigh v. Cohen, 983 F. Supp. 215, 216-17 (D.D.C. 1998)
Finding that U.S. Navy violated plaintiff's rights under ECPA, APA, Navy policy, and Fourth and Fifth Amendments by intercepting e-mail in which plaintiff referred to his homosexuality.
4. Internet Monitoring New York Law Journal July 2, 2002 http://www.bicklaw.com/Publications/Internet_Monitoring.htm
5. Lawful E- Medical Communications by Physicians New Jersey Medicine November 2002 http://www.bicklaw.com/Publications/Medical_e-mail.htm
6. e-HIPAA New Jersey Law Journal May 27, 2002 http://www.bicklaw.com/Publications/e-HIPAA.htm
Review Text Topics … Chapters 101
101.Taxes apply to Internet transactions
Schedule second feedback meetings
November 10 XII Internet "spin" on jurisdictional, regulatory and other issues
1. E-Land Transfer New York Law Journal, April 14, 1999 http://www.bicklaw.com/Publications/e-Land_transfer.htm
2. E Self Help New Jersey Law Journal September 30, 2002 http://www.bicklaw.com/Publications/e-self_help.htm
3. Zippo Mfg. Co. v. Zippo DOT Com, 952 F. Supp. 1119 (1997)
The court created a sliding scale of purposeful availment based on the interactivity of the defendant's Internet activities.
A complaint alleging trademark dilution, infringement and false designation. A motion to dismiss for lack of personal jurisdiction and improper venue, was made. Court found purposeful availment because Defendant had contracted with numerous individuals and Internet access providers in Pennsylvania and the intended object of the transactions had been the downloading of electronic messages that formed the basis of suit in Pennsylvania.
4. Top HR E-Laws New Jersey Law Journal June 9, 2003 http://www.bicklaw.com/Publications/Top_HR_e-laws.htm
5. E-Cyber Squatting New Jersey Law Journal December 2, 2002 http://www.bicklaw.com/Publications/e-cyber_squatting.htm
6. Patient e-Data Law New Jersey Law Journal March 25, 2002 http://www.bicklaw.com/Publications/Patient_e-data.htm
November 17 XIII Special topics and begin Class Presentations of Guided Research (10 minutes each) … peer critique
November 22 XIIII Special topics and begin Class Presentations of Guided Research (10 minutes each) … peer critique
Final papers must be handed in on the last day of Class
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||